4 Essential Facets of Cybersecurity to Pay Attention to
By Ashutosh Jha →
Friday, February 2, 2024
Whether you own a business, work for a company, or simply use the Internet for personal purposes, cybersecurity is more essential than ever in 2024. Cybersecurity acts as our defence against so many threats on the World Wide Web.
So much of our existence lies in the online space, that it’s become equally as important to protect our data as it is to protect our homes, health, and finances.
Here are some important aspects of cybersecurity that you need to know about in order to keep yourself and your business safe this year.
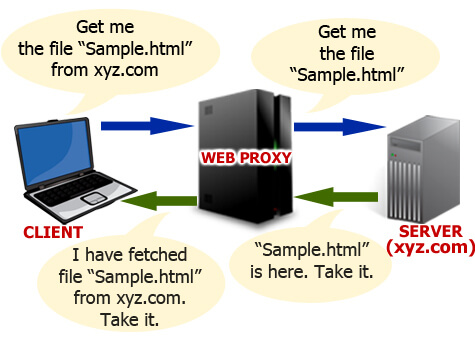
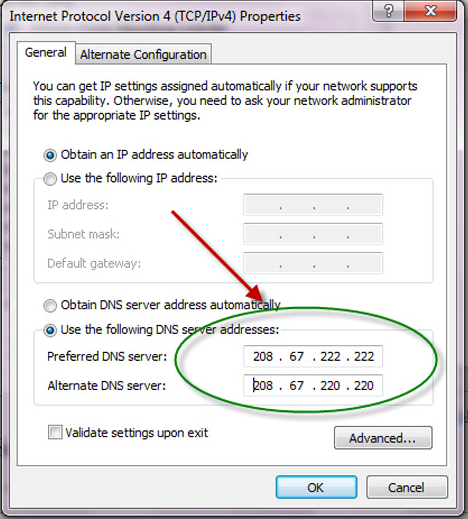
IP access control systems will check and limit the devices that can connect to your computer or network, only allowing trusted devices to protect your data and the integrity and security of your network. IP access control is usually integrated with other factors in a strategy, such as firewalls, encryption, etc.
You can secure your networks with various protective tactics such as firewalls and intrusion detection systems, which will create barriers and act as a watchdog for your system activities. It’s always a good idea to chat to a professional if you’re unsure of what software and systems to invest in.
First of all, you need to ensure you won’t accidentally lose this data by making sure that it’s backed up. Cloud storage is a great option, but having a physical copy as well could help you with peace of mind. You should also encrypt your sensitive data in case of any breach in your system and ensure to protect yourself against issues like DDoS attacks.
However, don’t forget to consider internal threats too – staff that has access to passwords and data could always take advantage of your trust, so make sure that the people you’re hiring are people you trust and that you keep any particularly sensitive information private and inaccessible if at all possible.
So much of our existence lies in the online space, that it’s become equally as important to protect our data as it is to protect our homes, health, and finances.
Here are some important aspects of cybersecurity that you need to know about in order to keep yourself and your business safe this year.
IP Access Control
Preventing unauthorized access to your device should always be front of mind. Of course, this means using a password and always keeping your smartphone, laptop, tablet, etc. on hand at all times. However, you also need to go further by thinking about other devices.IP access control systems will check and limit the devices that can connect to your computer or network, only allowing trusted devices to protect your data and the integrity and security of your network. IP access control is usually integrated with other factors in a strategy, such as firewalls, encryption, etc.
Network Security
When it comes to interconnected devices, networks facilitate and allow the flow of information. However, making sure that these networks are secure is essential. This is because securing your network is important for data protection, user privacy, and business continuity (since security breaches can seriously impact your productivity).You can secure your networks with various protective tactics such as firewalls and intrusion detection systems, which will create barriers and act as a watchdog for your system activities. It’s always a good idea to chat to a professional if you’re unsure of what software and systems to invest in.
Data Protection
If you’re working with any kind of sensitive data (as most of us are), you need to protect it. This applies to information related to your work, such as client information, or even personal details like your address and banking details.First of all, you need to ensure you won’t accidentally lose this data by making sure that it’s backed up. Cloud storage is a great option, but having a physical copy as well could help you with peace of mind. You should also encrypt your sensitive data in case of any breach in your system and ensure to protect yourself against issues like DDoS attacks.
Employee Training and Awareness
If you run a business and working with people, you need to make sure they’re as clued up as you are on cybersecurity. Everyone you work with will need to have some kind of access to your business network and data, so training your staff about workplace cyber threats is an essential factor to consider.However, don’t forget to consider internal threats too – staff that has access to passwords and data could always take advantage of your trust, so make sure that the people you’re hiring are people you trust and that you keep any particularly sensitive information private and inaccessible if at all possible.